by Joseph Forbes | Oct 8, 2021 | Blog, KnowledgeBase (KB), Maintenance, Troubleshooting, Updates, Web Hosting
Our MeshCentral is back online, all client MeshAgents reporting into the server as expected. Report – We performed updates to Windows Server 2019. After a restart, a service (IIS) kicked in, and took over Port 80. Node.js with it’s HTTP redirector changed...
by Joseph Forbes | Oct 8, 2021 | Blog Entry, KnowledgeBase (KB), Maintenance, Technical Support, Web Hosting
Determined the issue was the HTTP redirect service, detected the AD DS and a IIS instance running on Port 80. So even if we got MeshCentral settings fixed, Node.js service running the “wrapper” that hosts the MeshCentral website, kept detecting Port 80 in...
by Joseph Forbes | Jun 22, 2018 | Cloud Apps, DATA, KnowledgeBase (KB), Technical Support, Technicals, TECHNOLOGY
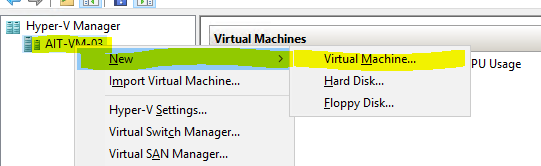
Creating a Hyper-V Template Creating a Hyper-V template to quickly deploy new VMs can save time on spin up and updating. You can set up hyper-V templates pre-installed with applications and Windows features just as a WDS or PXE image would provide a consistent...
by Joseph Forbes | Oct 28, 2017 | Blog Entry, HARDWARE, KnowledgeBase (KB), SECURITY, Technical Support, Technicals
Leave your computer on all the time, or shut it off when it’s not in use; does it really make a difference? If you’ve been asking yourself this question, then you’ll be happy to hear that you can choose whichever way you want. You just need to...
by Joseph Forbes | Oct 2, 2017 | Blog Entry, DATA, HARDWARE, INTERNET, KnowledgeBase (KB), Technicals, TECHNOLOGY
The latency of a network connection represents the amount of time required for data to travel between the sender and receiver. While all computer networks possess some inherent amount of latency, the amount varies and can suddenly increase for various reasons. People...
by Joseph Forbes | Sep 2, 2017 | Blog Entry, INTERNET, KnowledgeBase (KB), SECURITY, SOFTWARE, Technicals
All Windows computers include features that protect the operating system from hackers, viruses, and various types of malware. There are also protections in place to prevent mishaps that are brought on by the users themselves, such as the unintentional installation of...

